Market OverviewRising acceptance of the wearable technology, funds for executing digital technologies in the healthcare institutions, and the emergence of associated care are the significant factors improving the industry growth. Industrial advancements and rising geriatric population with the rising prevalence of various chronic conditions are further positively impacting market expansion.
According to research conducted by network provider company in the Aruba, closely 87% of healthcare organizations through the globe will adopt the IoT services by the year 2019. Researchers measured approximately 3,100 IT companies including business and healthcare decision-makers aroound 20 countries. The study concluded that the healthcare institutions have presented IoT for refining patient monitoring, promoting innovations, and decreasing costs.
Segment OverviewServices segment held largest market share in 2019. The segment is supplementary segmented into training, system integration services, and education, consulting, and support and maintenance. Growing demand for the uninterrupted data flows boost efficiency of medical systems, improve security, and enhance knowledgeable decision-making in real-time are the key factor propelling the services segment.
Furthermore, with the emergence of IoT services, dependency on the connected medical devices, including implantable, wearable, and stationary medical devices, for the health monitoring has augmented. Rising need for the connected health services for the critically ill patients, reduced cost of care, improved treatment outcomes, and the real-time disease management are the factors driving the IoT-enabled health devices market.
Regional OverviewNorth America dominated market in 2019. The growth is accredited to the rising adoption of various healthcare IT solutions, legislative initiatives, presence of key companies, regulations such as HITECH Law, 2009, and the availability of refined healthcare IT infrastructure in the region.
U.S. accounted for largest revenue share and is anticipated to maintain dominance over forecast period. Industrial advancements and numerous government initiatives encouraging the adoption of such digital platforms in the life science industry are main factors contributing to largest revenue share. There are several initiatives being accepted for developing clinical interoperability, and eHealth which is further driving the market.
Asia Pacific is anticipated to emerge as fastest-growing market. Growing health IT infrastructure, increasing initiatives for encouraging connected healthcare, and progressively increasing implementation of advanced technologies, inlcuding smart wearables, are key factors propelling the region’s growth. Rising investment by medical device and the pharmaceutical companies in the region is further expected to drive demand for the IoT technologies
.
Competitor overviewMicrosoft Corp.; Cisco Systems, Inc.; Koninklijke Philips N.V.; IBM Corp.; and Cerner Corp. are few of the major players in this market. Investments in R and D, collaborations with the other industry participants, and the service differentiation are important marketing strategies implemented by the companies. For instance, IBM collaborated with the Pfizer Inc., for developing system to develop clinical research process for the Parkinson’s disease in 2016.
Key Players
- Medtronic
- Koninklijke Philips N.V.
- General Electric Company
- IBM Corporation
- Microsoft
- Cerner Corporation
- Proteus Digital Health
- AdhereTech, Inc.
- Google
- Cisco System Ltd.
Market SegmentationBy Type
- Medical Devices
- Software & System
- Services
By Application
- Telemedicine
- Clinical Operations
- Inpatient Monitoring
- Medication Management
- Connected Imaging
- Others
By Technology
- Wi-Fi
- Near Field Communication (NFC)
- Bluetooth low energy
- ZigBee
- Cellular
- Satellite
By Geography
- North America
- Europe
- UK
- Germany
- France
- Italy
- Spain
- Rest of Europe
- Asia-Pacific
- Japan
- China
- India
- Australia
- South Korea
- Rest of Asia-Pacific
- LAMEA
- Brazil
- Saudi Arabia
- UAE
- Rest of LAMEA
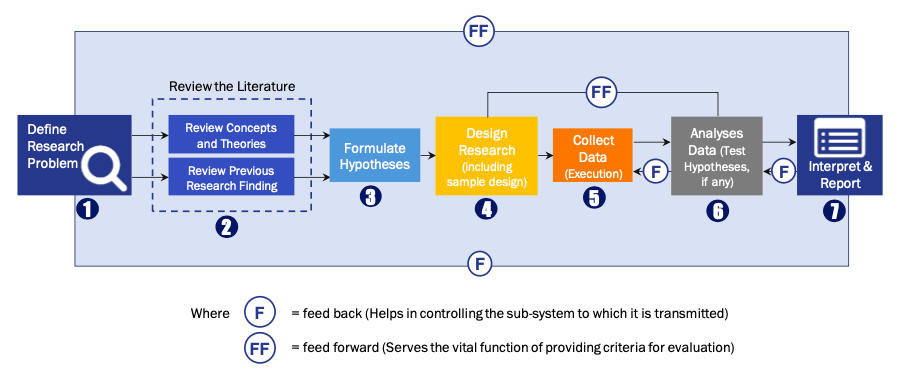
Research Process
Data Library Research are conducted by industry experts who offer insight on
industry structure, market segmentations technology assessment and competitive landscape (CL), and penetration, as well as on emerging trends. Their analysis is based on primary interviews (~ 80%) and secondary research (~ 20%) as well as years of professional expertise in their respective industries. Adding to this, by analysing historical trends and current market positions, our analysts predict where the market will be headed for the next five years. Furthermore, the varying trends of segment & categories geographically presented are also studied and the estimated based on the primary & secondary research.
In this particular report from the supply side Data Library Research has conducted primary surveys (interviews) with the key level executives (VP, CEO’s, Marketing Director, Business Development Manager
and SOFT) of the companies that active & prominent as well as the midsized organization
FIGURE 1: DLR RESEARH PROCESS
Primary Research
Extensive primary research was conducted to gain a deeper insight of the market and industry performance. The analysis is based on both primary and secondary research as well as years of professional expertise in the respective industries.
In addition to analysing current and historical trends, our analysts predict where the market is headed over the next five years.
It varies by segment for these categories geographically presented in the list of market tables. Speaking about this particular report we have conducted primary surveys (interviews) with the key level executives (VP, CEO’s, Marketing Director, Business Development Manager and many more) of the major players active in the market.
Secondary Research
Secondary research was mainly used to collect and identify information useful for the extensive, technical, market-oriented, and Friend’s study of the Global Extra Neutral Alcohol. It was also used to obtain key information about major players, market classification and segmentation according to the industry trends, geographical markets, and developments related to the market and technology perspectives. For this study, analysts have gathered information from various credible sources, such as annual reports, sec filings, journals, white papers, SOFT presentations, and company web sites.
Market Size Estimation
Both, top-down and bottom-up approaches were used to estimate and validate the size of the Global market and to estimate the size of various other dependent submarkets in the overall Extra Neutral Alcohol. The key players in the market were identified through secondary research and their market contributions in the respective geographies were determined through primary and secondary research.
Forecast Model